[Date Prev][Date Next][Thread Prev][Thread Next][Date Index][Thread Index]
Re: [Ftpapi] HTTPAPI help neded
Indeed, the DOJ had not provided us a complete URL for the service. We got that, so we are over that hump. Now I am dealing with other issues.
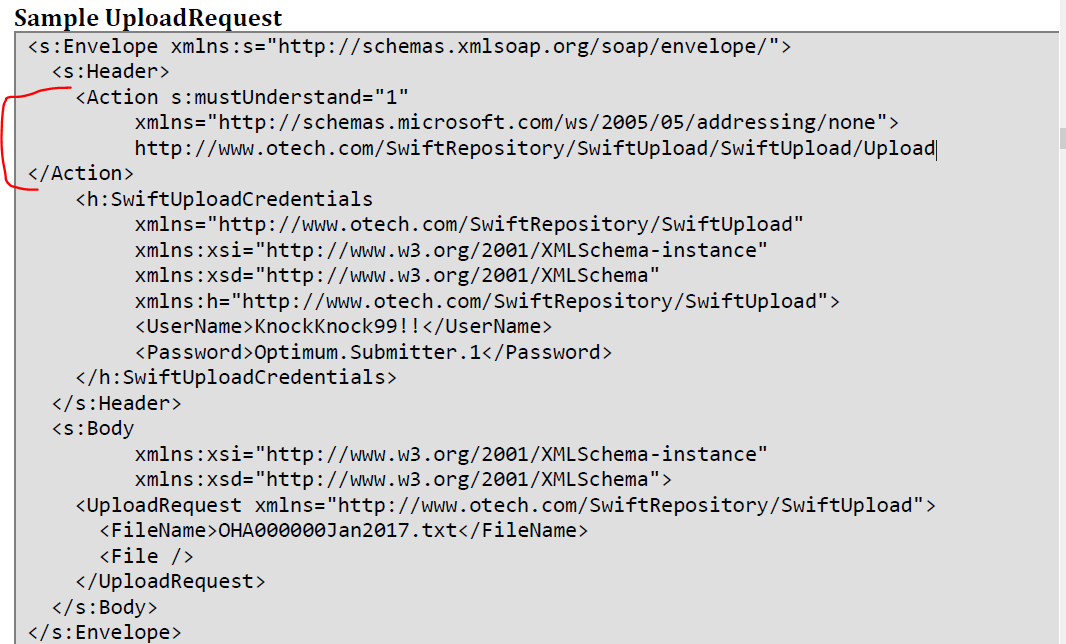
The SOAP envelope is confusing me. If I omit the "<Action> tag in the envelope, I get an HTTP 500 Error. If I include that tag formatted as it is shown in their example, I get an HTTP 400 error. I have tried every which way I can think of to format this differently, without success. I am suspecting there is something else I need to do with HTTPAPI to get this to work. I see things in the service program related to "SOAPAction", and I am wondering if this is something I need to set.
I have attached logs and the program source.
Ya, I see this a lot. Documentation doesn't keep up with the actual service endpoints. If I see a redirect, I always contact them and ask for the actual current endpoint.
Hi Scott,
I coded the redirect handling, which did what it was supposed to, but all I got was the actual login page echoed back to me. I'm thinking the CA DOJ hasn't given us the full and correct URL. How is their server supposed to know we are requesting a SOAP web service? Shouldn't the URL point us to that service, or at least a directory where services reside? In most examples I have seen, the URL points to the actual service. Is there some kind of "discovery" request I can make to find the service I need?
Again, thanks for your help.
Hi Braden,
It is sending you an HTTP 302 response. This means that it wants you to
to visit a different URL than the one you requested. In a web browser,
it would automatically visit the new URL, but in HTTPAPI, you have to
code the request to the new url yourself.
So it would be something like:
rc = http_req( parameter : parameter: etc);
if rc = 302;
rc = http_req( 'GET': http_redir_loc(): parameter: parameter);
endif;
So if you get a 302 response, you use http_redir_loc() to get the URL
its redirecting you to, and then you can make the new request against
that page.
Normally this doesn't come up with APIs, though... but, I'm not
familiar with this particular one, so maybe it's an exception to the rule?
-SK
On 11/6/2020 7:22 AM, Braden Lincoln wrote:
> I am a newbie on this. I am using HttpAPI to attempt to send a soap
> request that is supposed to download a file to the server. I am
> getting connected, and I can see my soap envelope being sent.
> Authentication is supposed to happen via the soap service, with the
> credentials being within the soap envelope. But I am getting
> redirected to a login page, rather than the soap service being
> invoked. VBelos is the full log. Any help would be appreciated.
> Thanks, Braden Lincoln
>
--
_______________________________________________
Ftpapi mailing list
Ftpapi@xxxxxxxxxxxxxxxxxxxxxx
http://scottklement.com/mailman/listinfo/ftpapi
_______________________________________________
Ftpapi mailing list
Ftpapi@xxxxxxxxxxxxxxxxxxxxxx
http://scottklement.com/mailman/listinfo/ftpapi
_______________________________________________
Ftpapi mailing list
Ftpapi@xxxxxxxxxxxxxxxxxxxxxx
http://scottklement.com/mailman/listinfo/ftpapi
**free
ctl-opt DFTACTGRP(*NO) BNDDIR('HTTPAPI') ACTGRP('QILE') ;
//
// Send request to CIBRS to upload file
//
//
/copy httpapi_h
dcl-f cibrresp disk usage(*output) rename(cibrresp:resp) ;
dcl-s url varchar(100) ;
dcl-s soap varchar(10000) ;
dcl-s myresponse varchar(16000000) ;
dcl-s logFile varchar(200) ;
dcl-s x int(10) ;
dcl-s y int(10) ;
dcl-s z int(10) ;
dcl-s myid int(10) ;
dcl-s rc int(10) ;
logFile = '/home/CIBRS/logs/http_api_log'+%char(%timestamp:*iso0)+'.txt' ;
http_debug(*on:logfile) ;
url = 'https://catraining.nibrs.com/SwiftUpload.svc' ; // their test site
soap =
'<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"; xmlns:swif="http://www.otech.com/SwiftRepository/SwiftUpload";>'+
'<soapenv:Header>'+
'<Action soapenv:mustUnderstand="1" xmlns="http://schemas.microsoft.com/ws/2005/05/addressing/none";>'+
' http://www.otech.com/SwiftRepository/SwiftUpload/SwiftUpload/Upload'+
'</Action>'+
'<swif:SwiftUploadCredentials>'+
'<swif:Password>aPassword</swif:Password>'+
'<swif:UserName>aUserName</swif:UserName>'+
'</swif:SwiftUploadCredentials>'+
'</soapenv:Header>'+
'<soapenv:Body>'+
'<swif:UploadRequest>'+
'<swif:ORINumber>CA0270700</swif:ORINumber>'+
'<swif:FileName>/home/CIBRS/requests/CIBR_NIBR202011010921</swif:FileName>'+
'</swif:UploadRequest>'+
'</soapenv:Body>'+
'</soapenv:Envelope>' ;
// good place to monitor for errors
// monitor ;
rc = http_req('POST':url:*omit:myresponse:*omit:soap:'text/xml') ;
if rc = 302 ;
rc = http_req('POST':http_redir_loc():*omit:myresponse:*omit:soap:'text/xml') ;
endif ;
// on-error ;
// *inlr = *on ;
// return ;
//endmon ;
// write the response to database table
response = %trim(myresponse) ;
write resp ;
// at this point, we would scan this string to see what "kind" of response we got, or we could parse the
// response XML document into a data structure, either way we will need to handle
// the responses
x=%scan('Success':myresponse) ;
if x > 0 ;
// the request was successful
// get the submission id from the upload request response (needed for checking status later)
y=%scan('<SubmissionID>':myresponse) ;
if y <> 0 ;
y +=14 ; // first byte of submission id
z=%scan('>':myresponse) ; // closing marker for submission id
z=z-y ; //length of id string
myid = %int(%subst(myresponse:y:z)) ; // myid contains the submission id of the file; this will need to be stored somewhere for later use
// store the id with the file name in "pending submissions" table??
endif;
else ;
x=%scan('Denied':myresponse) ;
if x > 0 ;
// login failed
else ;
x=%scan('Error':myresponse) ;
if x > 0 ;
// error sending data
else ;
x=%scan('Malformed':myresponse) ;
if x > 0 ;
// the request was malformed
endif ;
endif ;
endif ;
endif ;
*inlr = *on ; HTTPAPI Ver 1.42 released 2020-10-12
NTLM Ver 1.4.0 released 2014-12-22
OS/400 Ver V7R4M0
http_persist_open(): entered
http_long_ParseURL(): entered
DNS resolver retrans: 2
DNS resolver retry : 2
DNS resolver options: x'00000136'
DNS default domain: LOCAL.TECADATASAFE.COM
DNS server found: 8.8.8.8
Nagle's algorithm (TCP_NODELAY) disabled.
SNI hostname set to: catraining.nibrs.com
-------------------------------------------------------------------------------------
Dump of server-side certificate information:
-------------------------------------------------------------------------------------
Cert Validation Code = 6000
-----BEGIN CERTIFICATE-----
MIIG1jCCBb6gAwIBAgIJAPyMafwv/fv6MA0GCSqGSIb3DQEBCwUAMIG0MQswCQYD
VQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEa
MBgGA1UEChMRR29EYWRkeS5jb20sIEluYy4xLTArBgNVBAsTJGh0dHA6Ly9jZXJ0
cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzEzMDEGA1UEAxMqR28gRGFkZHkgU2Vj
dXJlIENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTE5MTIyMjEzNTQxMloX
DTIyMDIyMTAzNTgwMFowaDELMAkGA1UEBhMCVVMxDTALBgNVBAgTBE9oaW8xETAP
BgNVBAcTCENvbHVtYnVzMSEwHwYDVQQKExhPcHRpbXVtIFRlY2hub2xvZ3ksIElu
Yy4xFDASBgNVBAMMCyoubmlicnMuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A
MIIBCgKCAQEAuEs9aJJrerfJlexDZZd9+vjshPSINnumBa6diyTg6q4EnpVy5oh+
K7FardcihOdiWcu3h65X8DHDmRhnmdlX6tLjt+3Bp6L2vQuyyPbXdEaCTH7McqJx
u/tR5qaxXhh3n4ihF15UoFDySJqjvhiyEma4fX1cHxHECIfPRaSlfzwGZa3OZjNa
Q4Y7Kv/RpT2eb/+ym/kpIsTwaWsOuOmkgiztUzJNFGlFeFdsL/l2KqtmZOADo6Zt
sRNFwJowL0A/2TR8V/8DB6mdprF7hl4WsjPnAhLutZufNTHeNJGFmMu0g2O+NrJn
jlF7vZXUvcIj7PhqKXoaPZzYF6ZB3w/7TwIDAQABo4IDNDCCAzAwDAYDVR0TAQH/
BAIwADAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwDgYDVR0PAQH/BAQD
AgWgMDYGA1UdHwQvMC0wK6ApoCeGJWh0dHA6Ly9jcmwuZ29kYWRkeS5jb20vZ2Rp
ZzJzMi0xNC5jcmwwXQYDVR0gBFYwVDBIBgtghkgBhv1tAQcXAjA5MDcGCCsGAQUF
BwIBFitodHRwOi8vY2VydGlmaWNhdGVzLmdvZGFkZHkuY29tL3JlcG9zaXRvcnkv
MAgGBmeBDAECAjB2BggrBgEFBQcBAQRqMGgwJAYIKwYBBQUHMAGGGGh0dHA6Ly9v
Y3NwLmdvZGFkZHkuY29tLzBABggrBgEFBQcwAoY0aHR0cDovL2NlcnRpZmljYXRl
cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5L2dkaWcyLmNydDAfBgNVHSMEGDAWgBRA
wr0njsw0gzCiM9f7bLPwtCyAzjAhBgNVHREEGjAYggsqLm5pYnJzLmNvbYIJbmli
cnMuY29tMB0GA1UdDgQWBBQaWeZPY73/Cq8BguMCOpAgNdzXAzCCAX0GCisGAQQB
1nkCBAIEggFtBIIBaQFnAHcApLkJkLQYWBSHuxOizGdwCjw1mAT5G9+443fNDsgN
3BAAAAFvLeMPNgAABAMASDBGAiEAnHcr0YaOGI4v8If2wjxaQI3t77B3GYs053YT
/EF78VACIQDtA42mYTq+5vI6N+AKsetrMc7h9IBtJQIS2gQfi+MCfgB1AO5Lvbd1
zmC64UJpH6vhnmajD35fsHLYgwDEe4l6qP3LAAABby3jE6gAAAQDAEYwRAIgevSL
oG2m+pjDCTtwgFR2pFlDYVJ/GJwuCt8JJzMgarMCIEheLicsw9DbDKytHcv6Oh9c
4RtBVjx1FXmGxQYcfsddAHUAVhQGmi/XwuzT9eG9RLI+x0Z2ubyZEVzA75SYVdaJ
0N0AAAFvLeMVQgAABAMARjBEAiBLjuF0XaTvEl6tRm7gPUPJ+FxrCZSAmv/mYuGp
aengkAIgLyyo3r00TfWJMTRKh4PIbBmP+sAMC+MiP2TX8BOkeVQwDQYJKoZIhvcN
AQELBQADggEBAEhZwkJjDOrsZpkDtQyqBszGx2fUGPmlsQW3XLVkH9TbukxaLdTq
AH6eyHL7oiW9Q+1F/k6SW2MqwNFuWUnE9alfWTIPgKxZoHmAklyRkRna7TWK3JxO
X76EbUmCKjc4snh+NgSmNXo96o58/mug02eRLGy+rJ758AvL1WDysp0rIy+kfVHt
9gUzMJ/wgDRz5SlWEoT1wcBopI2n8nTaR04jaoo7s0y/r/jx7NIFbTUKcLcUIEqT
LTFZr4gkqGxorEpslo7ZtdZG82DoXNgtLV7EKY/jbEx0IVArBHm020ghnTCct0fh
YEwoPh7gDJ1m7eEuPim36fUHeG0HlsLZBSc=
-----END CERTIFICATE-----
Serial Number: 00:FC:8C:69:FC:2F:FD:FB:FA
Common Name: *.nibrs.com
Country: US
State/Province: Ohio
Locality: Columbus
Org Unit: Optimum Technology, Inc.
Issuer CN: Go Daddy Secure Certificate Authority - G2
Issuer Country: US
Issuer State/Province: Arizona
Issuer Locality: Scottsdale
Issuer Org: GoDaddy.com, Inc.
Issuer Org Unit: http://certs.godaddy.com/repository/
Version: 3
not before: 20191222055412
Unknown Field: 05:54:12 22-12-2019
not after: 20220220195800
Unknown Field: 19:58:00 20-02-2022
pub key alg: 1.2.840.113549.1.1.1
signature algorithm: 1.2.840.113549.1.1.11
Unknown Field: 0382010F003082010A0282010100B84B3D68926B7AB7C995EC4365977DFAF8EC84F488367BA605AE9D8B24E0EAAE049E9572E6887E2BB15AADD72284E76259CBB787AE57F031C399186799D957EAD2E3B7EDC1A7A2F6BD0BB2C8F6D77446824C7ECC72A271BBFB51E6A6B15E18779F88A1175E54A050F2489AA3BE18B21266B87D7D5C1F11C40887CF45A4A57F3C0665ADCE66335A43863B2AFFD1A53D9E6FFFB29BF92922C4F0696B0EB8E9A4822CED53324D14694578576C2FF9762AAB6664E003A3A66DB11345C09A302F403FD9347C57FF0307A99DA6B17B865E16B233E70212EEB59B9F3531DE34918598CBB48363BE36B2678E517BBD95D4BDC223ECF86A297A1A3D9CD817A641DF0FFB4F0203010001
Unknown Field: 2048
Unknown Field: 96B0F82452796E272042534E1EF72B6B
Unknown Field: 1.2.840.113549.2.5
Unknown Field: EF326B9ABD947820EB13AB9B3F4913CBFBCC8794
Unknown Field: 37BDE3AF9FC8481B81E079D64B146A1D254F3BFABE67B3C5BAEFC73F52AADCD0
Unknown Field: 5
Unknown Field: *.nibrs.com
Unknown Field: 0
Unknown Field: 1.3.6.1.5.5.7.3.2
Unknown Field: 1.3.6.1.5.5.7.3.1
Unknown Field: 2.23.140.1.2.2
Unknown Field: 2.16.840.1.114413.1.7.23.2
Unknown Field: http://ocsp.godaddy.com/
Protocol Used: TLS Version 1.2
http_persist_req(POST) entered.
http_long_ParseURL(): entered
http_long_ParseURL(): entered
do_oper(POST): entered
There are 2 cookies in the cache
POST /SwiftUpload.svc HTTP/1.1
Host: catraining.nibrs.com
User-Agent: http-api/1.43
Content-Type: text/xml
Content-Length: 565
Cookie: $Version=0; ARRAffinity=ceb254e931dc3c85fc581cb9af526dbcc121f61ab18fb7cf2b6bedf4e7c3ab97; $Path=/; $Domain=catraining.nibrs.com; $Version=0; ARRAffinitySameSite=ceb254e931dc3c85fc581cb9af526dbcc121f61ab18fb7cf2b6bedf4e7c3ab97; $Path=/; $Domain=catraining.nibrs.com;
senddoc(): entered
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"; xmlns:swif="http://www.otech.com/SwiftRepository/SwiftUpload";><soapenv:Header><Action soapenv:mustUnderstand="1"></Action><swif:SwiftUploadCredentials><swif:Password>aPassword</swif:Password><swif:UserName>aUserName</swif:UserName></swif:SwiftUploadCredentials></soapenv:Header><soapenv:Body><swif:UploadRequest><swif:ORINumber>CA0270700</swif:ORINumber><swif:FileName>/home/CIBRS/requests/CIBR_NIBR202011010921</swif:FileName></swif:UploadRequest></soapenv:Body></soapenv:Envelope>
recvresp(): entered
HTTP/1.1 500 Internal Server Error
Cache-Control: no-cache, no-store
Pragma: no-cache
Content-Length: 698
Content-Type: text/xml; charset=utf-8
Expires: -1
Server: Microsoft-IIS/10.0
X-Frame-Options: SAMEORIGIN
X-AspNet-Version: 4.0.30319
X-Powered-By: ASP.NET
Date: Tue, 10 Nov 2020 17:53:45 GMT
SetError() #13: HTTP/1.1 500 Internal Server Error
recvresp(): end with 500
recvdoc parms: identity 698
header_load_cookies() entered
recvdoc(): entered
SetError() #0:
recvdoc(): Receiving 698 bytes.
<s:Envelope xmlns:s="http://schemas.xmlsoap.org/soap/envelope/";><s:Body><s:Fault><faultcode xmlns:a="http://schemas.microsoft.com/ws/2005/05/addressing/none";>a:ActionNotSupported</faultcode><faultstring xml:lang="en-US">The message with Action '' cannot be processed at the receiver, due to a ContractFilter mismatch at the EndpointDispatcher. This may be because of either a contract mismatch (mismatched Actions between sender and receiver) or a binding/security mismatch between the sender and the receiver. Check that sender and receiver have the same contract and the same binding (including security requirements, e.g. Message, Transport, None).</faultstring></s:Fault></s:Body></s:Envelope>
SetError() #13: HTTP/1.1 500 Internal Server Error
http_close(): entered
HTTPAPI Ver 1.42 released 2020-10-12
NTLM Ver 1.4.0 released 2014-12-22
OS/400 Ver V7R4M0
New iconv() objects set, PostRem=819. PostLoc=0. ProtRem=819. ProtLoc=0
http_persist_open(): entered
http_long_ParseURL(): entered
DNS resolver retrans: 2
DNS resolver retry : 2
DNS resolver options: x'00000136'
DNS default domain: LOCAL.TECADATASAFE.COM
DNS server found: 8.8.8.8
https_init(): entered
QSSLPCL = *TLSV1.3 *TLSV1.2 *SSLV3
SSL version 2 support disabled
SSL version 3 support disabled
Old interface to TLS version 1.0 support enabled
TLS version 1.0 support enabled
TLS version 1.1 support enabled
TLS version 1.2 support enabled
initializing GSK environment
GSK Environment now available
-------------------------------------------------------------------------------------
Dump of local-side certificate information:
-------------------------------------------------------------------------------------
Nagle's algorithm (TCP_NODELAY) disabled.
SNI hostname set to: catraining.nibrs.com
-------------------------------------------------------------------------------------
Dump of server-side certificate information:
-------------------------------------------------------------------------------------
Cert Validation Code = 6000
-----BEGIN CERTIFICATE-----
MIIG1jCCBb6gAwIBAgIJAPyMafwv/fv6MA0GCSqGSIb3DQEBCwUAMIG0MQswCQYD
VQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEa
MBgGA1UEChMRR29EYWRkeS5jb20sIEluYy4xLTArBgNVBAsTJGh0dHA6Ly9jZXJ0
cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzEzMDEGA1UEAxMqR28gRGFkZHkgU2Vj
dXJlIENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTE5MTIyMjEzNTQxMloX
DTIyMDIyMTAzNTgwMFowaDELMAkGA1UEBhMCVVMxDTALBgNVBAgTBE9oaW8xETAP
BgNVBAcTCENvbHVtYnVzMSEwHwYDVQQKExhPcHRpbXVtIFRlY2hub2xvZ3ksIElu
Yy4xFDASBgNVBAMMCyoubmlicnMuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A
MIIBCgKCAQEAuEs9aJJrerfJlexDZZd9+vjshPSINnumBa6diyTg6q4EnpVy5oh+
K7FardcihOdiWcu3h65X8DHDmRhnmdlX6tLjt+3Bp6L2vQuyyPbXdEaCTH7McqJx
u/tR5qaxXhh3n4ihF15UoFDySJqjvhiyEma4fX1cHxHECIfPRaSlfzwGZa3OZjNa
Q4Y7Kv/RpT2eb/+ym/kpIsTwaWsOuOmkgiztUzJNFGlFeFdsL/l2KqtmZOADo6Zt
sRNFwJowL0A/2TR8V/8DB6mdprF7hl4WsjPnAhLutZufNTHeNJGFmMu0g2O+NrJn
jlF7vZXUvcIj7PhqKXoaPZzYF6ZB3w/7TwIDAQABo4IDNDCCAzAwDAYDVR0TAQH/
BAIwADAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwDgYDVR0PAQH/BAQD
AgWgMDYGA1UdHwQvMC0wK6ApoCeGJWh0dHA6Ly9jcmwuZ29kYWRkeS5jb20vZ2Rp
ZzJzMi0xNC5jcmwwXQYDVR0gBFYwVDBIBgtghkgBhv1tAQcXAjA5MDcGCCsGAQUF
BwIBFitodHRwOi8vY2VydGlmaWNhdGVzLmdvZGFkZHkuY29tL3JlcG9zaXRvcnkv
MAgGBmeBDAECAjB2BggrBgEFBQcBAQRqMGgwJAYIKwYBBQUHMAGGGGh0dHA6Ly9v
Y3NwLmdvZGFkZHkuY29tLzBABggrBgEFBQcwAoY0aHR0cDovL2NlcnRpZmljYXRl
cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5L2dkaWcyLmNydDAfBgNVHSMEGDAWgBRA
wr0njsw0gzCiM9f7bLPwtCyAzjAhBgNVHREEGjAYggsqLm5pYnJzLmNvbYIJbmli
cnMuY29tMB0GA1UdDgQWBBQaWeZPY73/Cq8BguMCOpAgNdzXAzCCAX0GCisGAQQB
1nkCBAIEggFtBIIBaQFnAHcApLkJkLQYWBSHuxOizGdwCjw1mAT5G9+443fNDsgN
3BAAAAFvLeMPNgAABAMASDBGAiEAnHcr0YaOGI4v8If2wjxaQI3t77B3GYs053YT
/EF78VACIQDtA42mYTq+5vI6N+AKsetrMc7h9IBtJQIS2gQfi+MCfgB1AO5Lvbd1
zmC64UJpH6vhnmajD35fsHLYgwDEe4l6qP3LAAABby3jE6gAAAQDAEYwRAIgevSL
oG2m+pjDCTtwgFR2pFlDYVJ/GJwuCt8JJzMgarMCIEheLicsw9DbDKytHcv6Oh9c
4RtBVjx1FXmGxQYcfsddAHUAVhQGmi/XwuzT9eG9RLI+x0Z2ubyZEVzA75SYVdaJ
0N0AAAFvLeMVQgAABAMARjBEAiBLjuF0XaTvEl6tRm7gPUPJ+FxrCZSAmv/mYuGp
aengkAIgLyyo3r00TfWJMTRKh4PIbBmP+sAMC+MiP2TX8BOkeVQwDQYJKoZIhvcN
AQELBQADggEBAEhZwkJjDOrsZpkDtQyqBszGx2fUGPmlsQW3XLVkH9TbukxaLdTq
AH6eyHL7oiW9Q+1F/k6SW2MqwNFuWUnE9alfWTIPgKxZoHmAklyRkRna7TWK3JxO
X76EbUmCKjc4snh+NgSmNXo96o58/mug02eRLGy+rJ758AvL1WDysp0rIy+kfVHt
9gUzMJ/wgDRz5SlWEoT1wcBopI2n8nTaR04jaoo7s0y/r/jx7NIFbTUKcLcUIEqT
LTFZr4gkqGxorEpslo7ZtdZG82DoXNgtLV7EKY/jbEx0IVArBHm020ghnTCct0fh
YEwoPh7gDJ1m7eEuPim36fUHeG0HlsLZBSc=
-----END CERTIFICATE-----
Serial Number: 00:FC:8C:69:FC:2F:FD:FB:FA
Common Name: *.nibrs.com
Country: US
State/Province: Ohio
Locality: Columbus
Org Unit: Optimum Technology, Inc.
Issuer CN: Go Daddy Secure Certificate Authority - G2
Issuer Country: US
Issuer State/Province: Arizona
Issuer Locality: Scottsdale
Issuer Org: GoDaddy.com, Inc.
Issuer Org Unit: http://certs.godaddy.com/repository/
Version: 3
not before: 20191222055412
Unknown Field: 05:54:12 22-12-2019
not after: 20220220195800
Unknown Field: 19:58:00 20-02-2022
pub key alg: 1.2.840.113549.1.1.1
signature algorithm: 1.2.840.113549.1.1.11
Unknown Field: 0382010F003082010A0282010100B84B3D68926B7AB7C995EC4365977DFAF8EC84F488367BA605AE9D8B24E0EAAE049E9572E6887E2BB15AADD72284E76259CBB787AE57F031C399186799D957EAD2E3B7EDC1A7A2F6BD0BB2C8F6D77446824C7ECC72A271BBFB51E6A6B15E18779F88A1175E54A050F2489AA3BE18B21266B87D7D5C1F11C40887CF45A4A57F3C0665ADCE66335A43863B2AFFD1A53D9E6FFFB29BF92922C4F0696B0EB8E9A4822CED53324D14694578576C2FF9762AAB6664E003A3A66DB11345C09A302F403FD9347C57FF0307A99DA6B17B865E16B233E70212EEB59B9F3531DE34918598CBB48363BE36B2678E517BBD95D4BDC223ECF86A297A1A3D9CD817A641DF0FFB4F0203010001
Unknown Field: 2048
Unknown Field: 96B0F82452796E272042534E1EF72B6B
Unknown Field: 1.2.840.113549.2.5
Unknown Field: EF326B9ABD947820EB13AB9B3F4913CBFBCC8794
Unknown Field: 37BDE3AF9FC8481B81E079D64B146A1D254F3BFABE67B3C5BAEFC73F52AADCD0
Unknown Field: 5
Unknown Field: *.nibrs.com
Unknown Field: 0
Unknown Field: 1.3.6.1.5.5.7.3.2
Unknown Field: 1.3.6.1.5.5.7.3.1
Unknown Field: 2.23.140.1.2.2
Unknown Field: 2.16.840.1.114413.1.7.23.2
Unknown Field: http://ocsp.godaddy.com/
Protocol Used: TLS Version 1.2
http_persist_req(POST) entered.
http_long_ParseURL(): entered
http_long_ParseURL(): entered
do_oper(POST): entered
There are 0 cookies in the cache
POST /SwiftUpload.svc HTTP/1.1
Host: catraining.nibrs.com
User-Agent: http-api/1.43
Content-Type: text/xml
Content-Length: 697
senddoc(): entered
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"; xmlns:swif="http://www.otech.com/SwiftRepository/SwiftUpload";><soapenv:Header><Action soapenv:mustUnderstand="1" xmlns="http://schemas.microsoft.com/ws/2005/05/addressing/none";> http://www.otech.com/SwiftRepository/SwiftUpload/SwiftUpload/Upload</Action><swif:SwiftUploadCredentials><swif:Password>aPassword</swif:Password><swif:UserName>aUserName</swif:UserName></swif:SwiftUploadCredentials></soapenv:Header><soapenv:Body><swif:UploadRequest><swif:ORINumber>CA0270700</swif:ORINumber><swif:FileName>/home/CIBRS/requests/CIBR_NIBR202011010921</swif:FileName></swif:UploadRequest></soapenv:Body></soapenv:Envelope>
recvresp(): entered
HTTP/1.1 400 Bad Request
Cache-Control: no-cache, no-store
Pragma: no-cache
Expires: -1
Server: Microsoft-IIS/10.0
X-Frame-Options: SAMEORIGIN
X-AspNet-Version: 4.0.30319
X-Powered-By: ASP.NET
Set-Cookie: ARRAffinity=ceb254e931dc3c85fc581cb9af526dbcc121f61ab18fb7cf2b6bedf4e7c3ab97;Path=/;HttpOnly;Secure;Domain=catraining.nibrs.com
Set-Cookie: ARRAffinitySameSite=ceb254e931dc3c85fc581cb9af526dbcc121f61ab18fb7cf2b6bedf4e7c3ab97;Path=/;HttpOnly;SameSite=None;Secure;Domain=catraining.nibrs.com
Date: Tue, 10 Nov 2020 21:26:19 GMT
Content-Length: 0
SetError() #13: HTTP/1.1 400 Bad Request
recvresp(): end with 400
recvdoc parms: identity 0
header_load_cookies() entered
cookie_parse() entered
cookie = ARRAffinity=ceb254e931dc3c85fc581cb9af526dbcc121f61ab18fb7cf2b6bedf4e7c3ab97;Path=/;HttpOnly;Secure;Domain=catraining.nibrs.com
cookie attr ARRAffinity=ceb254e931dc3c85fc581cb9af526dbcc121f61ab18fb7cf2b6bedf4e7c3ab97
cookie attr Path=/
cookie attr HttpOnly=
cookie attr Secure=
cookie attr Domain=catraining.nibrs.com
cookie_parse() entered
cookie = ARRAffinitySameSite=ceb254e931dc3c85fc581cb9af526dbcc121f61ab18fb7cf2b6bedf4e7c3ab97;Path=/;HttpOnly;SameSite=None;Secure;Domain=catraining.nibrs.com
cookie attr ARRAffinitySameSite=ceb254e931dc3c85fc581cb9af526dbcc121f61ab18fb7cf2b6bedf4e7c3ab97
cookie attr Path=/
cookie attr HttpOnly=
cookie attr SameSite=None
cookie attr Secure=
cookie attr Domain=catraining.nibrs.com
recvdoc(): entered
SetError() #0:
recvdoc(): Receiving 0 bytes.
recvdoc(): Nothing to receive, exiting...
SetError() #13: HTTP/1.1 400 Bad Request
http_close(): entered
--
_______________________________________________
Ftpapi mailing list
Ftpapi@xxxxxxxxxxxxxxxxxxxxxx
http://scottklement.com/mailman/listinfo/ftpapi